
One of the best features of Linux server is IPTables , For Network Engineers who are looking to understand the complexities in technology like eBPF, IPTables is an familiar starting point where the concepts like Packet Handling in the Kernel. I want to outline some details but bring it back to some practical use cases . My goal is to provide some practical iptables use but to also explains the tables in iptables and it actually functions.
IPTables Basics
Lets start with the basics, First of all iptables is a well basically a firewall , it helps control traffic policy across a device. How can I see some basics about iptables ?
| Command | Description |
| iptables -L | List all “Firewall” Filter Rules |
| iptables -L –line-numbers -v | List all Filter rules with line numbers and number of packets that have hit the rule |
| iptables -I INPUT 3 -p icmp -j ACCEPT | Insert Accept ICMP to INPUT Table for rule number 3 |
| iptables -A INPUT -m conntrack –ctstate RELATED,ESTABLISHED -j ACCEPT | append rule to table for all related or established connections |
| iptables -I INPUT 1 -m conntrack –ctstate RELATED,ESTABLISHED -j ACCEPT | same rule only INSERTING it to position 1 of the input table |
| iptables -A INPUT -j LOG –log-prefix “iptables INPUT: ” –log-level 4 | log events in syslog |
| iptables-save | save iptables config changes |
| iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE | Simple NAT all traffic to eth0s ip address (ideal for public ip) |
| iptables -P INPUT DROP | default deny INPUT |
| iptables -P OUTPUT DROP | default deny OUTPUT |
| iptables -P FORWARD DROP | default deny FORWARD |
Below is an example of the FILTER table and two CHAINS Input and Forward
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
num pkts bytes target prot opt in out source destination
1 30 2000 ACCEPT all -- any any anywhere anywhere ctstate RELATED,ESTABLISHED
2 17M 170G LIBVIRT_INP all -- any any anywhere anywhere
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
num pkts bytes target prot opt in out source destination
1 196K 14M DOCKER-USER all -- any any anywhere anywhere
2 196K 12M DOCKER-ISOLATION-STAGE-1 all -- any any anywhere anywhere
3 0 0 ACCEPT all -- any br-812f849fdf89 anywhere anywhere ctstate RELATED,ESTABLISHED
4 0 0 DOCKER all -- any br-812f849fdf89 anywhere anywhere
5 196K 12M ACCEPT all -- br-812f849fdf89 !br-812f849fdf89 anywhere anywhere
6 0 0 ACCEPT all -- br-812f849fdf89 br-812f849fdf89 anywhere anywhere
7 0 0 ACCEPT all -- any docker0 anywhere anywhere ctstate RELATED,ESTABLISHED
8 0 0 DOCKER all -- any docker0 anywhere anywhere
9 0 0 ACCEPT all -- docker0 !docker0 anywhere anywhere
10 0 0 ACCEPT all -- docker0 docker0 anywhere anywhere
11 0 0 LIBVIRT_FWX all -- any any anywhere anywhere
12 0 0 LIBVIRT_FWI all -- any any anywhere anywhere
13 0 0 LIBVIRT_FWO all -- any any anywhere anywhere
Tables , Chains & Rules

Now There is Multiple tables in IPTables , right so what are they?
The most common is filter since that is responsible for the traditional IP Tuple of Firewall access but there is 5 in total FILTER , NAT , MANGLE , RAW , SECURITY
| Table | Command to view | Description |
| Filter | iptables -t filter -L | Accepts / Rejects Packets |
| NAT | iptables -t nat -L | used to modify the source or destination IP addresses. |
| Mangle | iptables -t mangle -L | can perform general-purpose editing of packet headers, but it is not intended for NAT |
| Raw | iptables -t raw -L | allows for packet mutation before connection tracking and other tables are handled |
| Security | iptables -t security -L | SELinux uses the Security table for packet handling |
Now that we understand there is multiple tables , we need to know about the different chains inside each table. Important is to understand iptables was created jointly with Netfilter. Netfilter is a framework of kernel hooks which allow userspace programs to handle packets on behalf of the kernel. Netfilter has 5 Hooks and those hooks are chains
| Netfilter Hook | Iptables chain | Description |
| NF_IP_PRE_ROUTING | PREROUTING | Triggers when a packer arrives from an external system |
| NF_IP_LOCAL_IN | INPUT | When packet is destined for ip on the machine |
| NF_IP_FORWARD | FORWARD | Packets where src/dst is NOT machine IP. Machine is routing on behalf |
| NF_IP_LOCAL_OUT | OUTPUT | Packet originating from machine leaves |
| NF_IP_POST_ROUTING | POSTROUTING | When ANY packet leaves the machine |
Examples of Packets through tables , chains and rules
The last idea I want to share is that not every tables has every chain since the purposes vary on the context. Last item is lets look at some examples, lets start with a topology from Netlab We are going to focus on the left side of the diagram Servers H3 and Server1 are running Ubuntu with IPTables enforcement. Devices ISP1 and LABSW1 are running FRR BGP and act as routers in this build
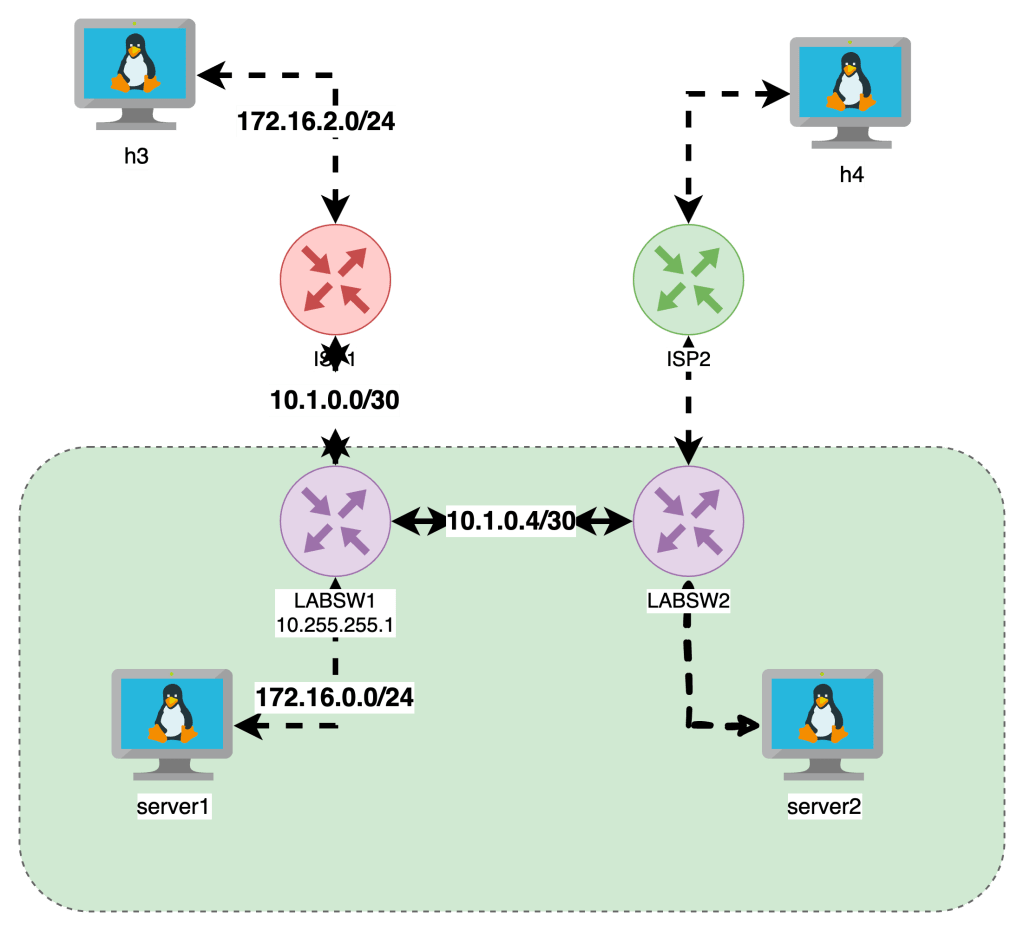
Here is the iptables on server1
server1:/# iptables -L -v --line-numbers
# Warning: iptables-legacy tables present, use iptables-legacy to see them
Chain INPUT (policy DROP 69 packets, 5796 bytes)
num pkts bytes target prot opt in out source destination
1 2409 3203K ACCEPT all -- any any anywhere anywhere ctstate RELATED,ESTABLISHED
2 0 0 REJECT tcp -- any any anywhere anywhere state INVALID reject-with icmp-port-unreachable
3 1 84 ACCEPT icmp -- any any anywhere anywhere
4 75 6268 LOG all -- any any anywhere anywhere LOG level warn prefix "iptables INPUT: "
5 74 6184 LOG all -- any any anywhere anywhere LOG level warn prefix "iptables INPUT: "
Chain FORWARD (policy DROP 0 packets, 0 bytes)
num pkts bytes target prot opt in out source destination
Chain OUTPUT (policy DROP 3 packets, 252 bytes)
num pkts bytes target prot opt in out source destination
1 9 756 ACCEPT icmp -- any any anywhere anywhere
The INPUT , NAT & OUTPUT have DENY as the default Rule as well as explicit allow rules for ICMP traffic to allow for this example
Server1 has ip 172.16.0.5 and is pinging across to h3 172.16.2.7. The INPUT table shows packets hit for RELATED and ESTABLISHED as well as the OUTPUT table
This is the basics of iptables and look for my next post that expands on these topics.
