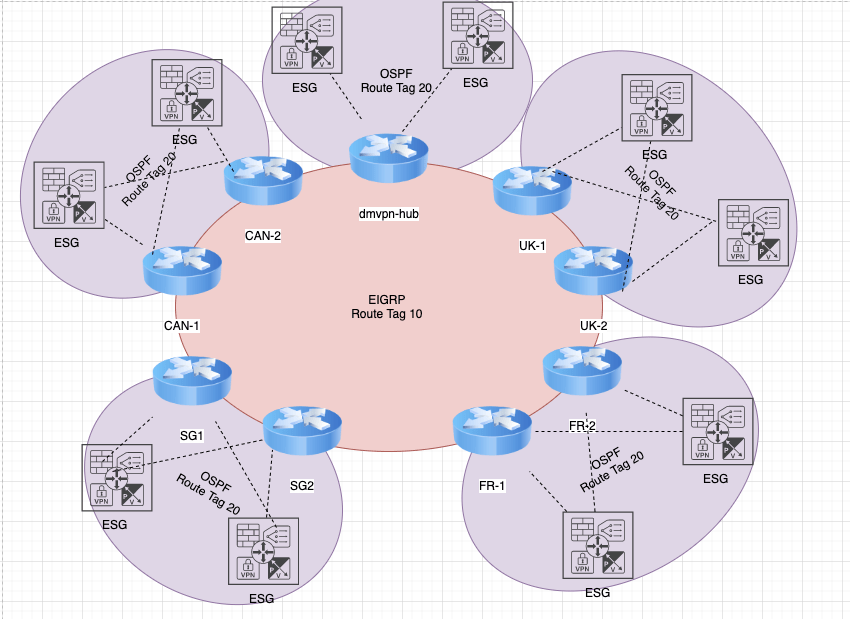
This week has been centered all around DMVPN & VMWare NSX. Earlier in the week , I was addressing an issues with routing loops observed . In the deployment I have two spokes in Canada that are Cisco 6504-E devices. The control plane for EIGRP come up with neighborships between the Hub and Spokes. Routes are passed from the Spokes down the ESG in the local envrionment , however data plane traffic is not successful. I see traffic leave the ESG and hit the local edge and then die. When I remove the encryption map. The traffic routes successfully.
I consulted with Cisco TAC who advised the configuration should be supported, but when running a packet capture the only issue observed is that encrypted traffic never even enters the local vlan interface . This is when I decided to apply some ACLs on the local vlan interface to see if any traffic was arriving.
Even stranger once I applied these ACLs to with the “log-input” command traffic across the environment began to work. I am waiting on Cisco TAC to advise on why this works. I removed the log-input from the ACL which seems to break the data plane again.
Cisco TAC responded and apparently the log-input forces all the traffic to he software switched instead of CEF which allows the traffic to pass. Cisco advises that the C6500 does not support DMVPN without a SPA Carrier Module.